Application Security Posture Management
Monitor & Harden Security Posture for Your Applications
In today’s rapidly evolving digital landscape, applications are growing more complex, being developed at a faster pace, and involving diverse teams. A robust Application Security Posture Management (ASPM) system is critical for defending your cloud-native applications. BoostSecurity’s platform offers a comprehensive security boost across the entire application lifecycle, ensuring that your applications are secure from development to production.
BoostSecurity for Application Security Posture Management
Complete Pipeline Visibility
Critical Risk Prioritization
Full SDLC Protection
Complete Pipeline Visibility
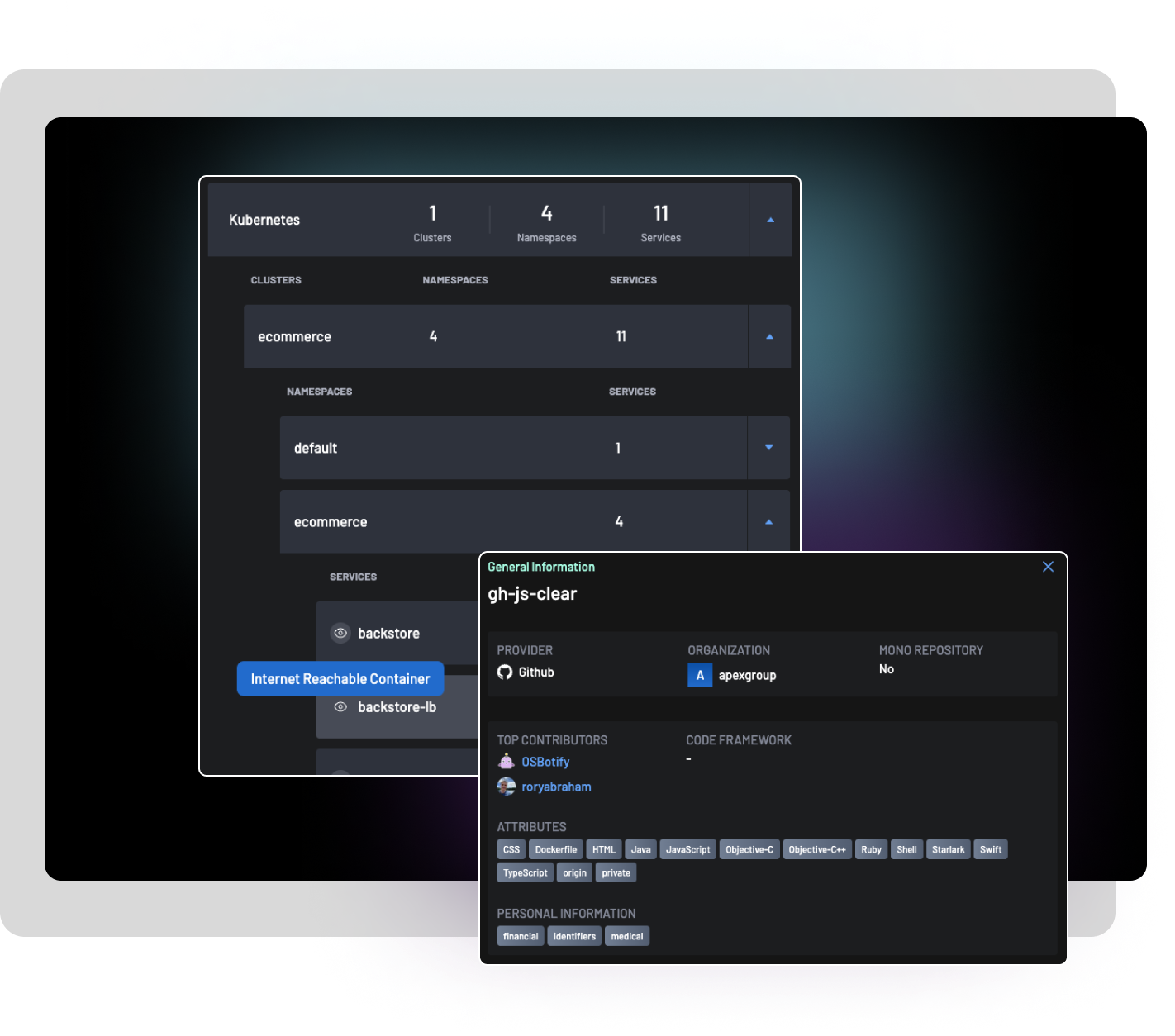
With BoostSecurity, gain complete pipeline visibility by generating a queryable inventory of all components in your software pipelines, including GitHub apps, developer accounts, CI plugins, and more. This provides the insight needed to identify vulnerabilities before they become risks.
Answer questions like:
- Which CI systems are used across our development infrastructure?
- Which GitHub apps are installed?
- Which CI plugins have known vulnerabilities?
- Where are we using LLM technology in our code?
- Which repos are missing security scanning?
- Which repositories define APIs and touch PII data?
Critical Risk Prioritization
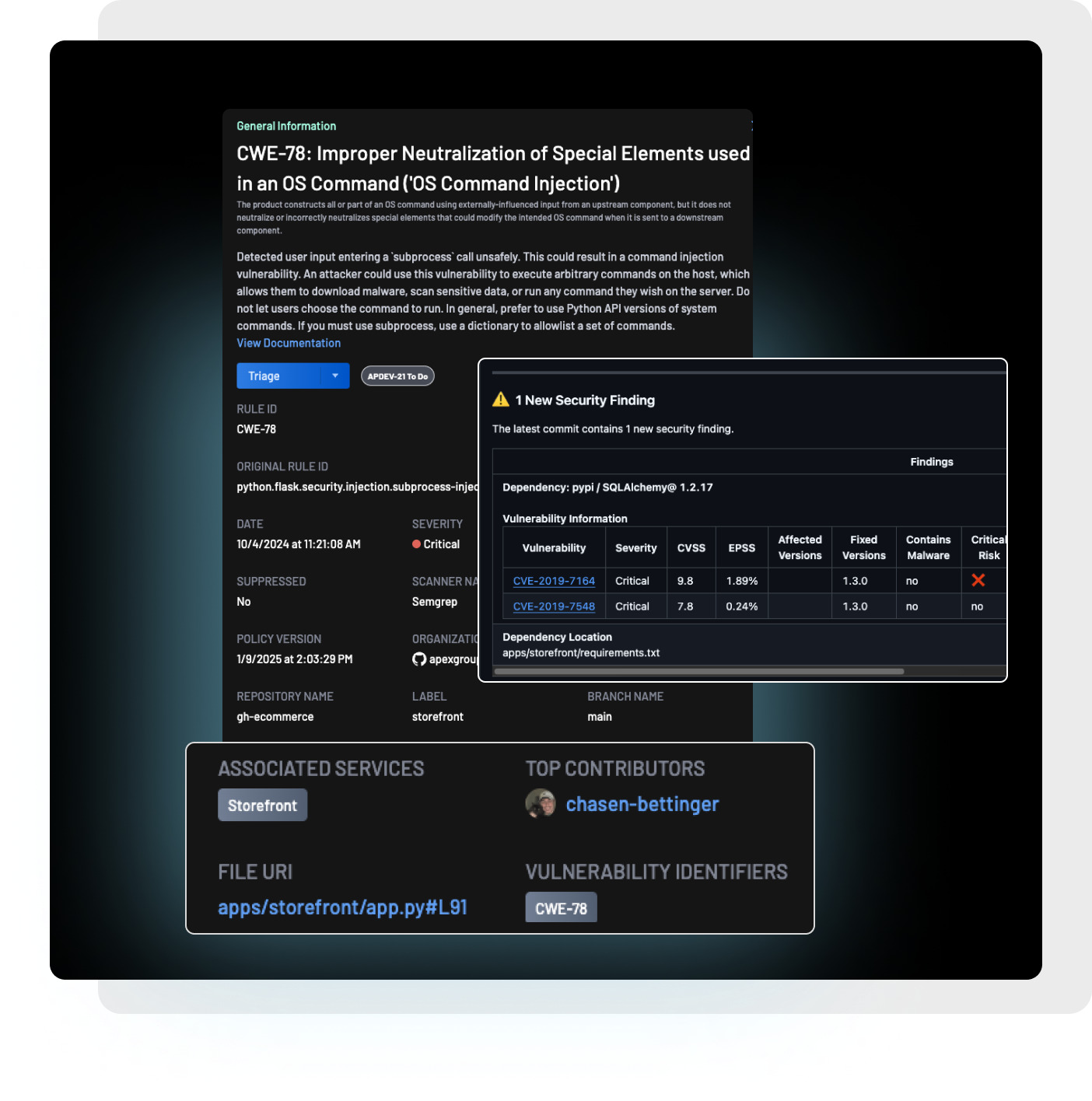
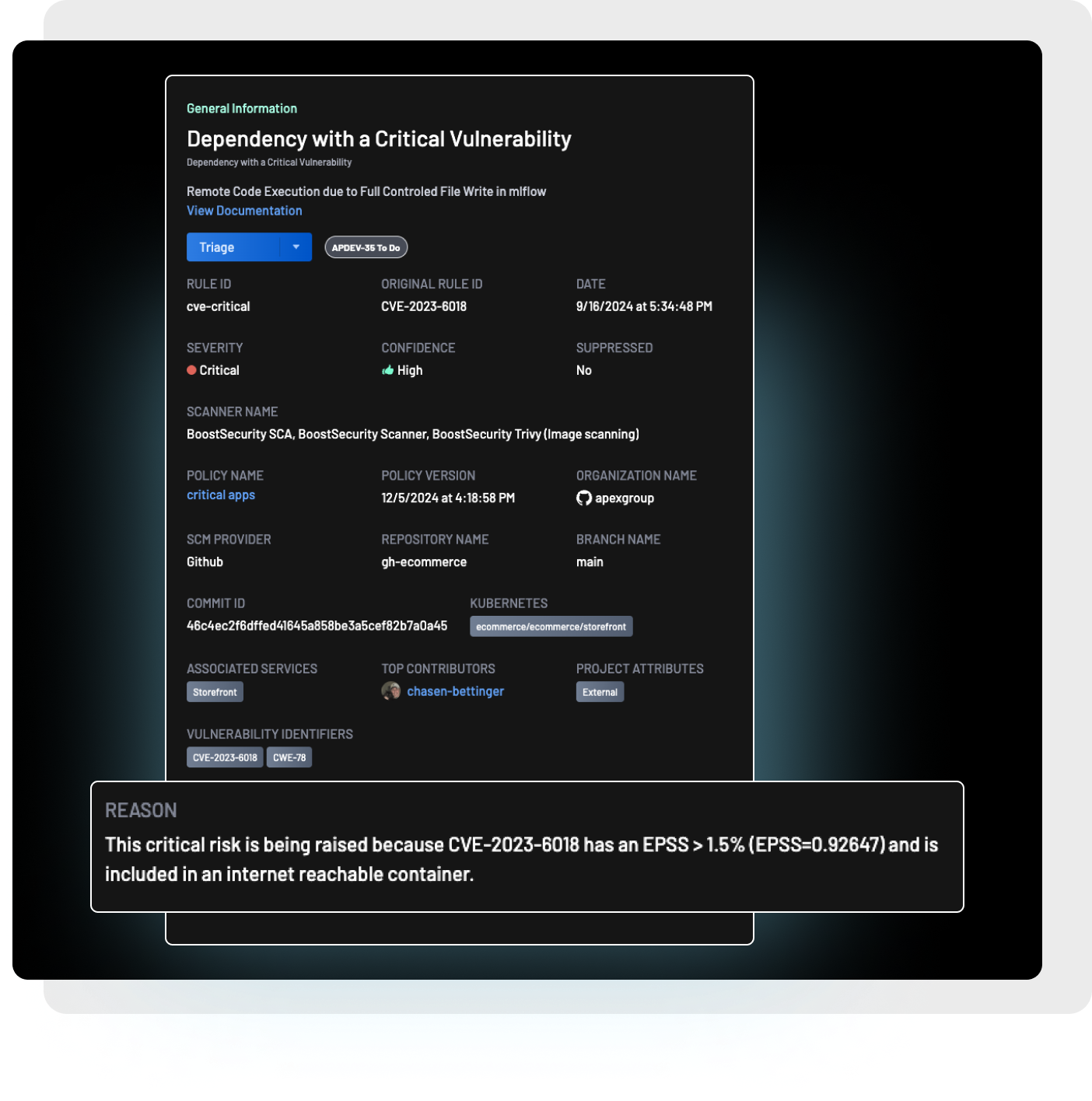
Security tools generate a lot of data. That is a fact of life. Triaging everything is a waste of everyone's time. With BoostSecurity, you can focus your efforts on actual exploitable risks like;- A SQL injection that affects PII data and is internet reachable
- An active CVE in a critical service that is internet facing
- An active secret hardcoded in a public repository
- An open source repo with an exploitable weakness in its configuration
Full SDLC Protection
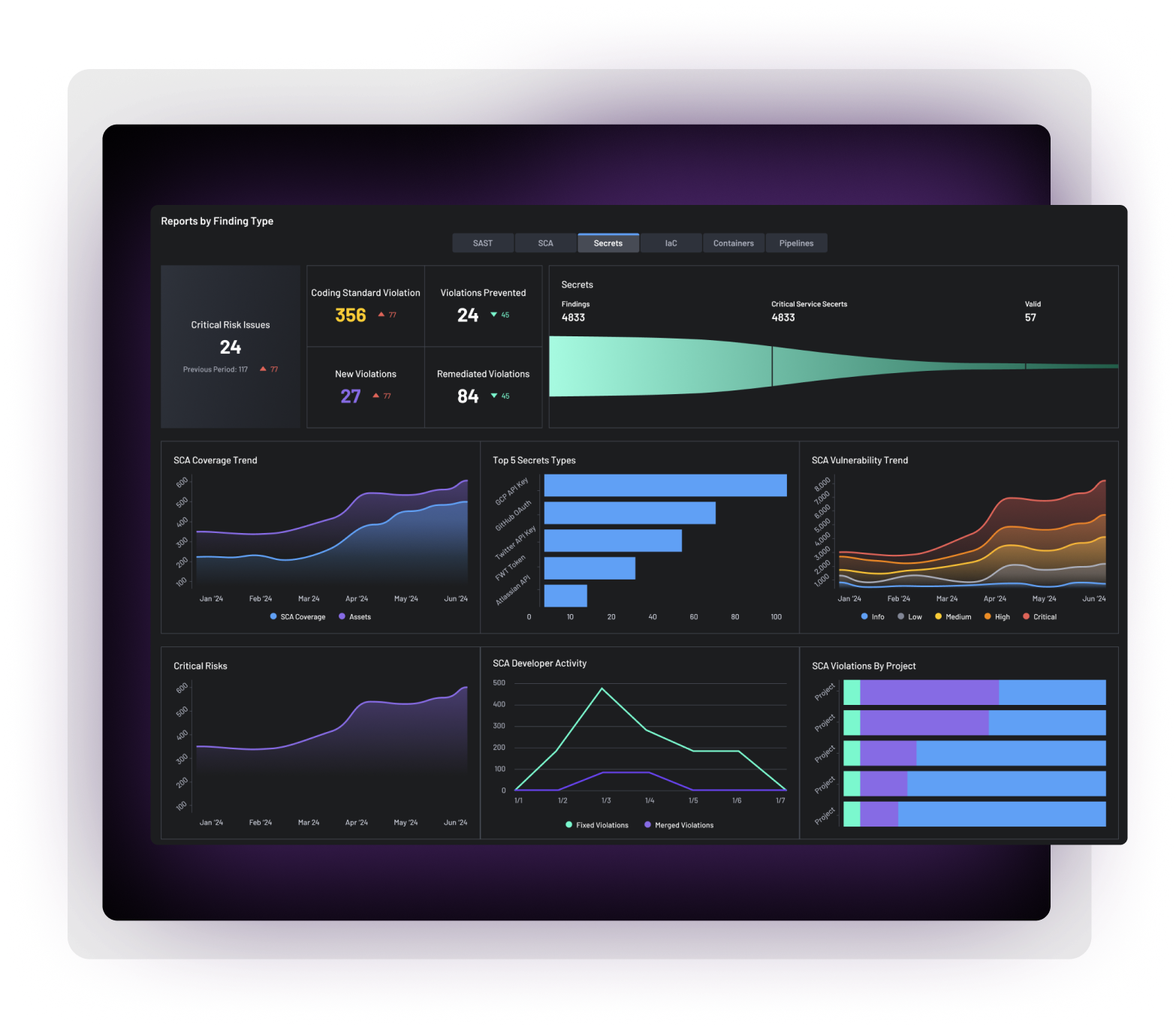
Understand how vulnerabilities and weaknesses detected at develop and build time are affecting you at runtime. BoostSecurity connects the information from both runtime and build environments so you can;
Understand how vulnerabilities and weaknesses detected at develop and build time are affecting you at runtime. BoostSecurity connects the information from both runtime and build environments so you can;
- Speed up triage by prioritizing vulnerabilities detected at runtime
- Provide necessary context for developers to remediate
- Set develop time policy based on runtime context
- Gate your production systems based on develop time information

See how BoostSecurity for Application Security Posture Management works
Frequently Asked Questions
Ask our
Customer Support
Our development environment is extremely complex with multiple teams and tech stacks. Can BoostSecurity handle this?
Yes. BoostSecurity is designed specifically for complex, multi-team environments. Our platform automatically discovers and inventories all components across your software pipelines, regardless of technology stack diversity. The queryable inventory provides unified visibility without requiring standardization of your existing tools.
How long does it take to get complete visibility across our entire development infrastructure?
BoostSecurity's discovery process typically provides comprehensive pipeline visibility within hours of deployment. The automated inventory generation means you don't need to manually catalog your infrastructure components or wait for lengthy assessment periods.
We're drowning in security alerts. How does BoostSecurity actually reduce alert fatigue?
BoostSecurity's Critical Risk Prioritization engine contextualizes findings based on real exploitability. Instead of generic vulnerability lists, you get prioritized risks like "SQL injection in internet-facing service handling PII data." This means your team focuses only on threats that pose actual business risk.
Will this create more work for our developers?
It reduces developer workload. By providing contextual information and identifying the root cause location for fixes, developers spend less time investigating and more time solving. The platform shows exactly where to fix issues and provides the necessary context for efficient remediation.
How is our sensitive development information protected?
All data is encrypted in transit and at rest. BoostSecurity follows enterprise security standards and provides detailed audit logs. You maintain control over data access and can configure exactly what information is shared with the platform.
We're a large enterprise with thousands of repositories. Will BoostSecurity scale?
Yes. BoostSecurity is built for enterprise scale and handles environments with thousands of repositories, multiple cloud providers, and diverse technology stacks. The queryable inventory system is designed to provide fast insights regardless of infrastructure size.
No FAQs found
Try adjusting your search terms or clear the search