Software Supply Chain Security
Developers and software development infrastructure are
direct targets for cyber attacks.
Protect against attackers dropping malware into open source packages, abusing misconfigured SCM
and CI systems, stealing your developer credentials and tokens, injecting backdoors into your code,
and stealing your IP.
BoostSecurity for Software Supply Chain Protection
Instant Observability
Get complete visibility across your software supply chain including;-
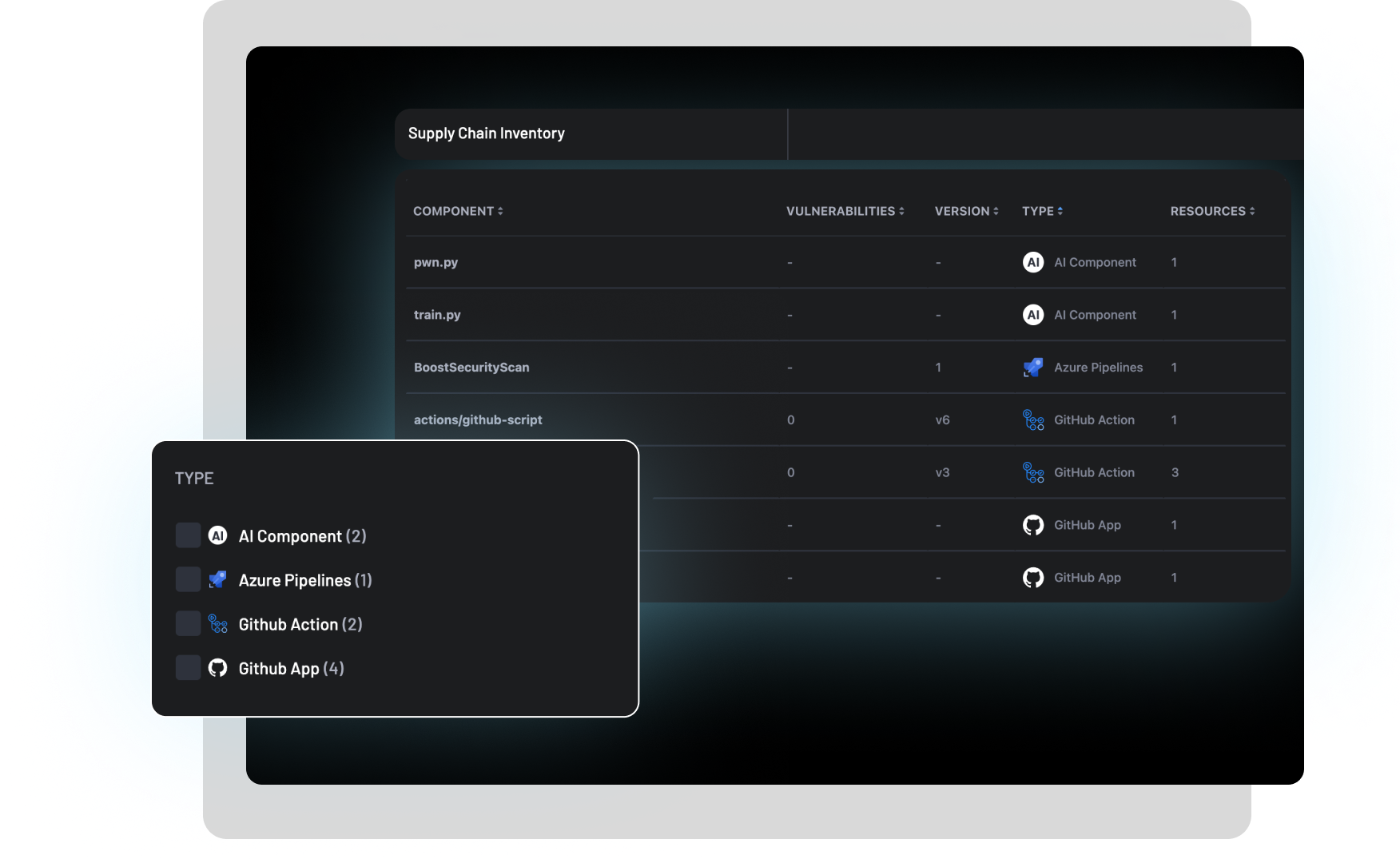
- SCM and CI systems
- Tools being used in the pipeline
- CI plugins
- Webhooks registered
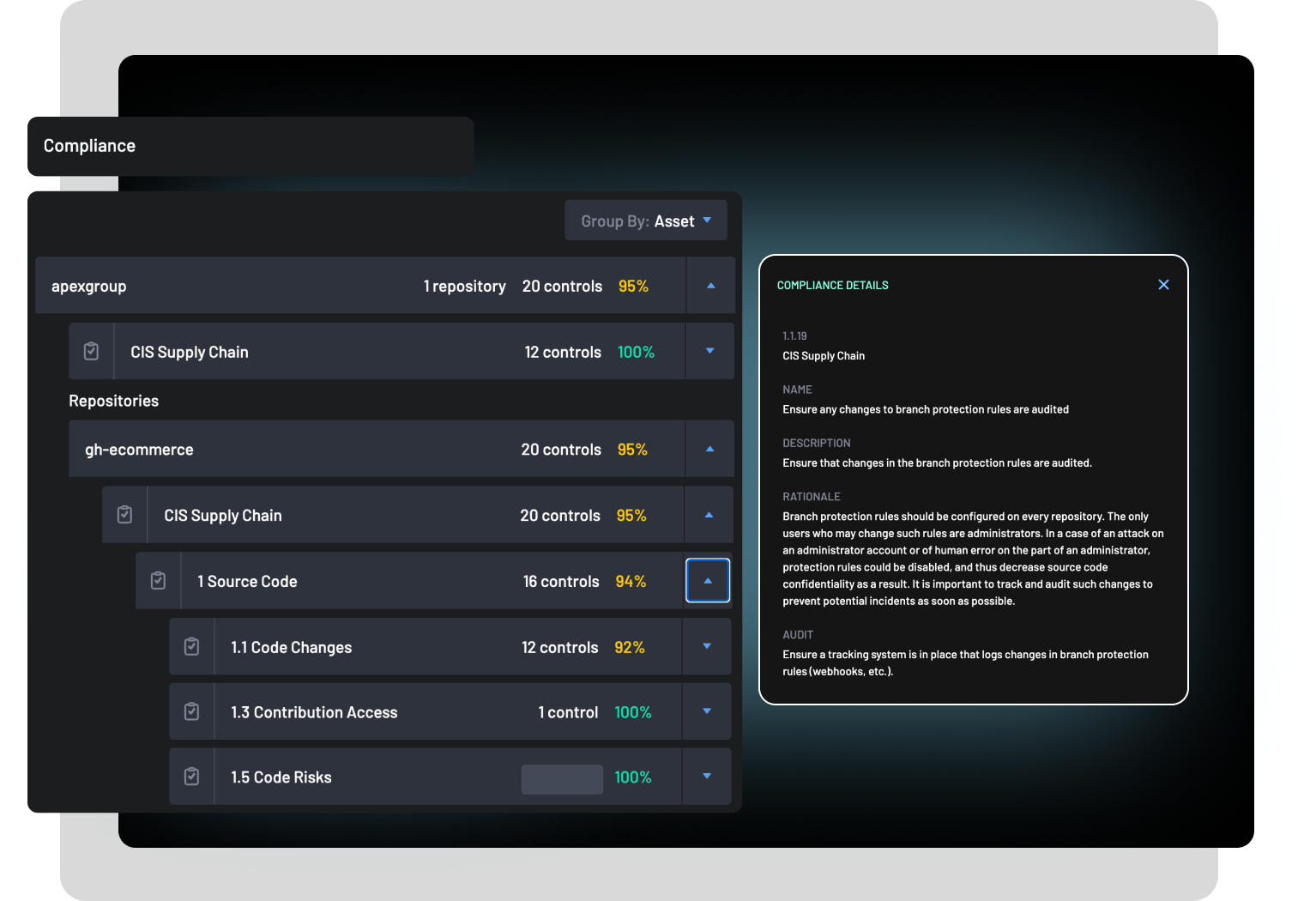
- Developer access to repositories
BoostSecurity inventories your entire SDLC infrastructure, allowing you to easily apply policy and report based on what is in the pipeline, as well as easily investigate the impact of known vulnerabilities.
Mitigate Exploitable Weaknesses
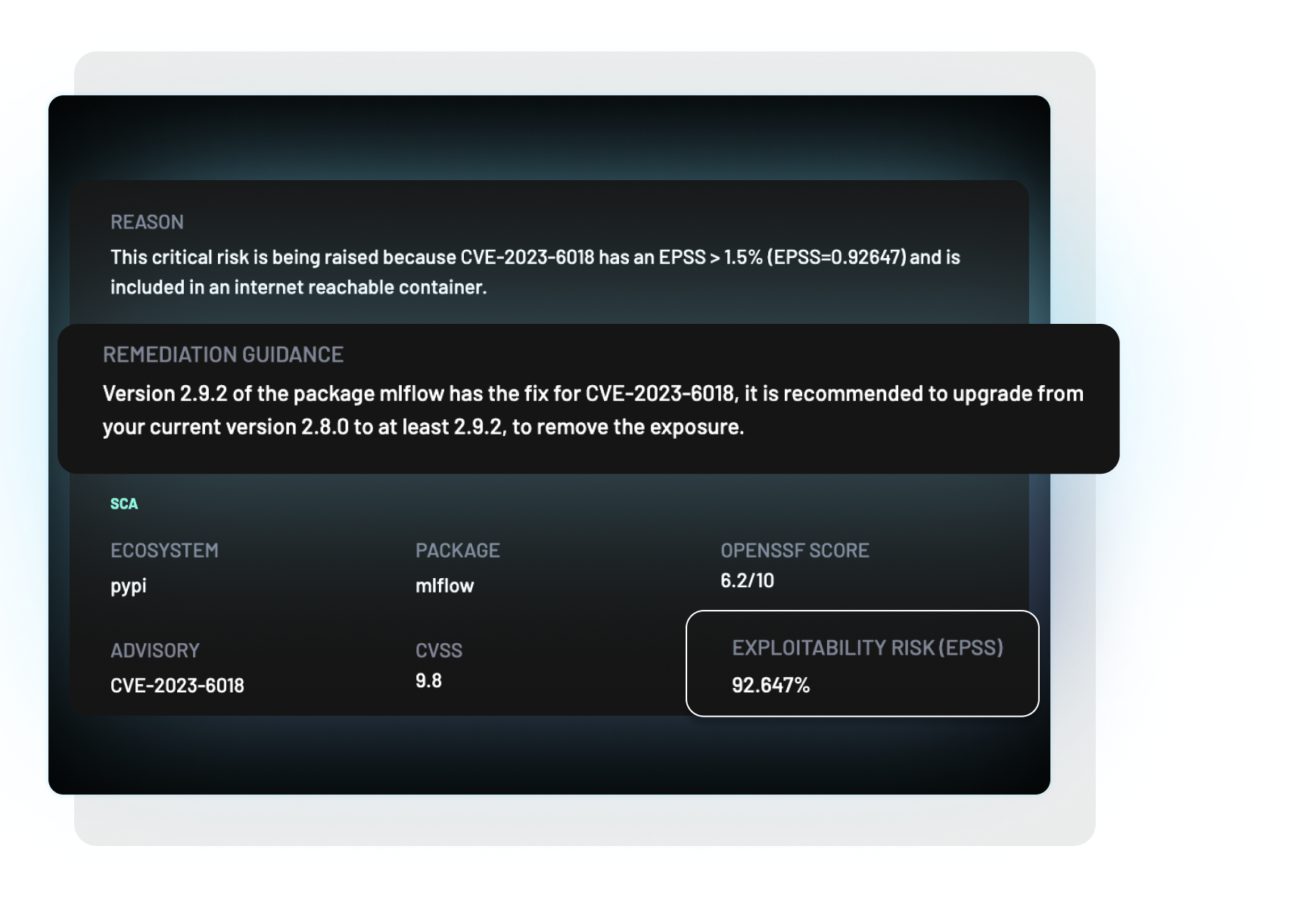
Detect security weaknesses in your development infrastructure, including;- OSS package malware
- OSS repository maintenance practices
- SCM configurations
- Source code access controls
- CVEs
- CI script vulnerabilities
BoostSecurity will detect these and many more types of security weaknesses in your development infrastructure and guide you to remediate.

Blog: Attacks on Popular GitHub Actions
Recent attacks on popular GitHub Actions (tj-actions/changed-files and reviewdog/action-setup) have shocked us, but not surprised us.
Read Now
CISO & CTO Guide to Supply Chain Security
While there are plenty of supply chain security standards and deeply technical resources, this guide is intended to fill a gap. It approaches supply chain risk at the business level, and reveals how these attacks materialize.
Get My Copy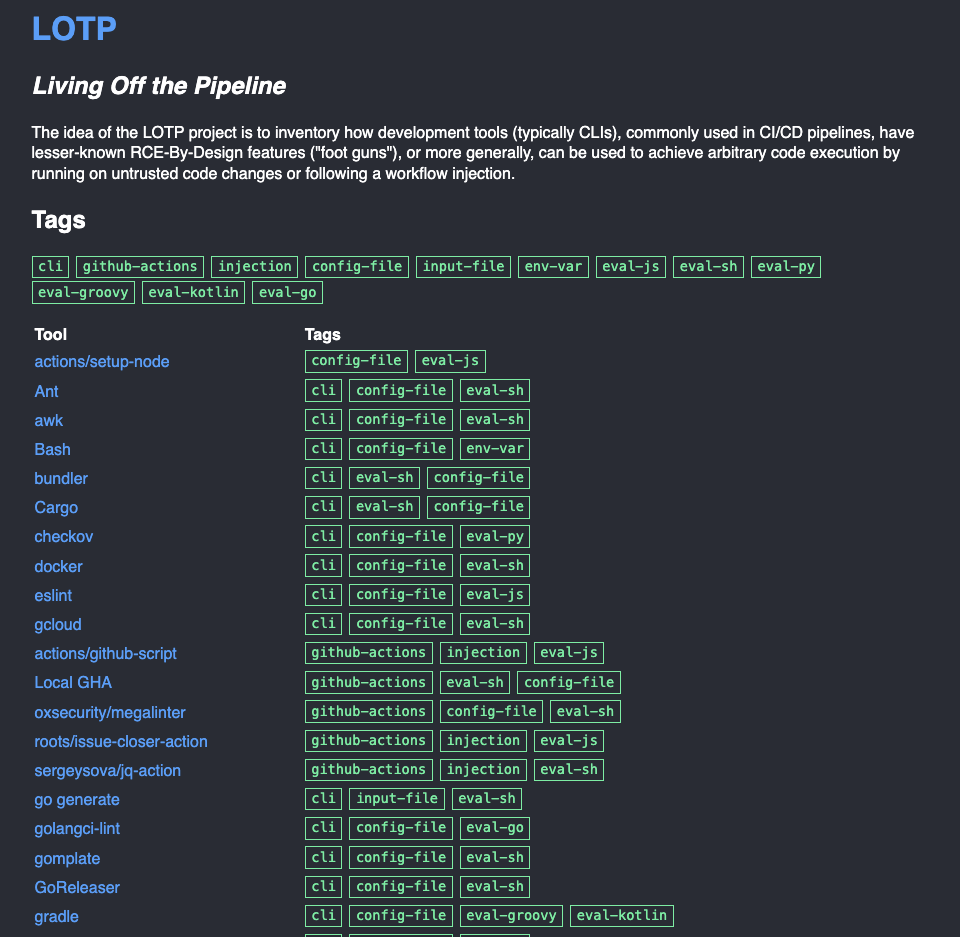
GitHub: Living Off The Pipeline
BoostSecurity's Research team catalogues tools which can be used to inject arbitrary code to execute in existing build pipelines. We validate and test each scenario listed in this interactive resource.
Explore Exploitable Tools