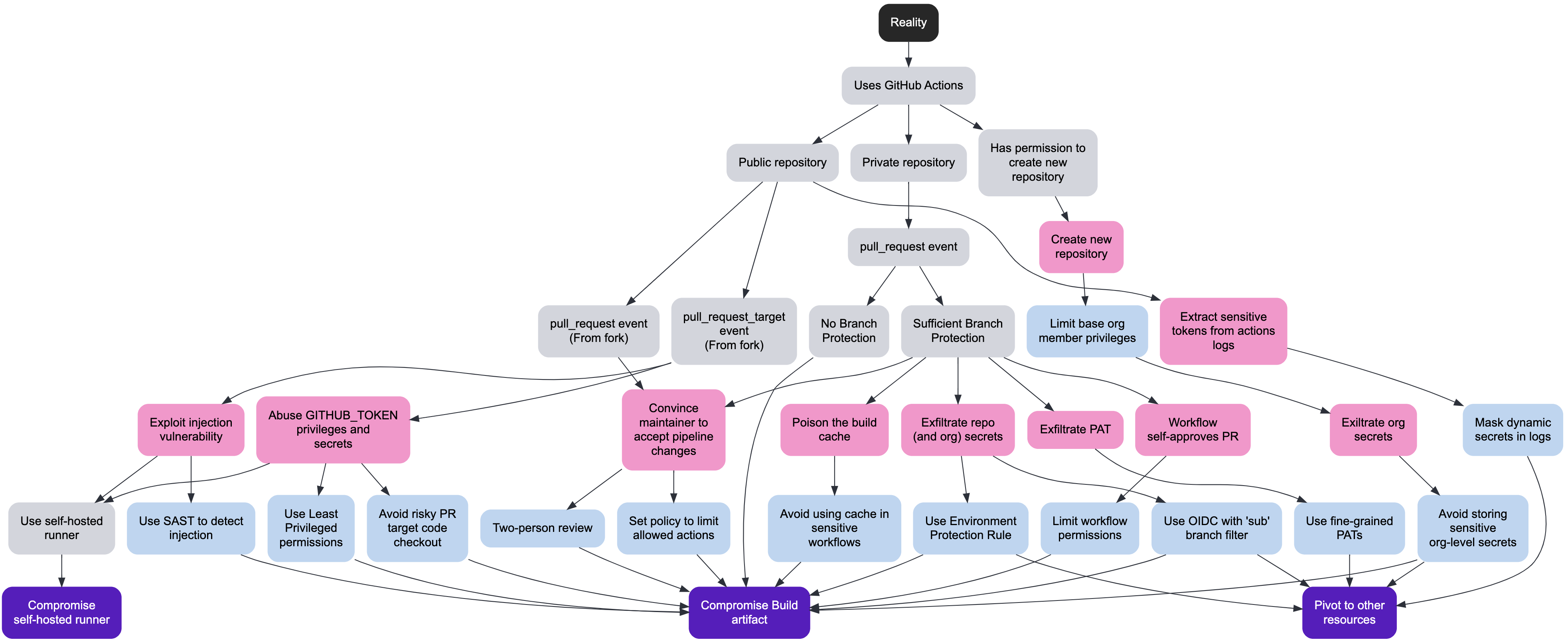
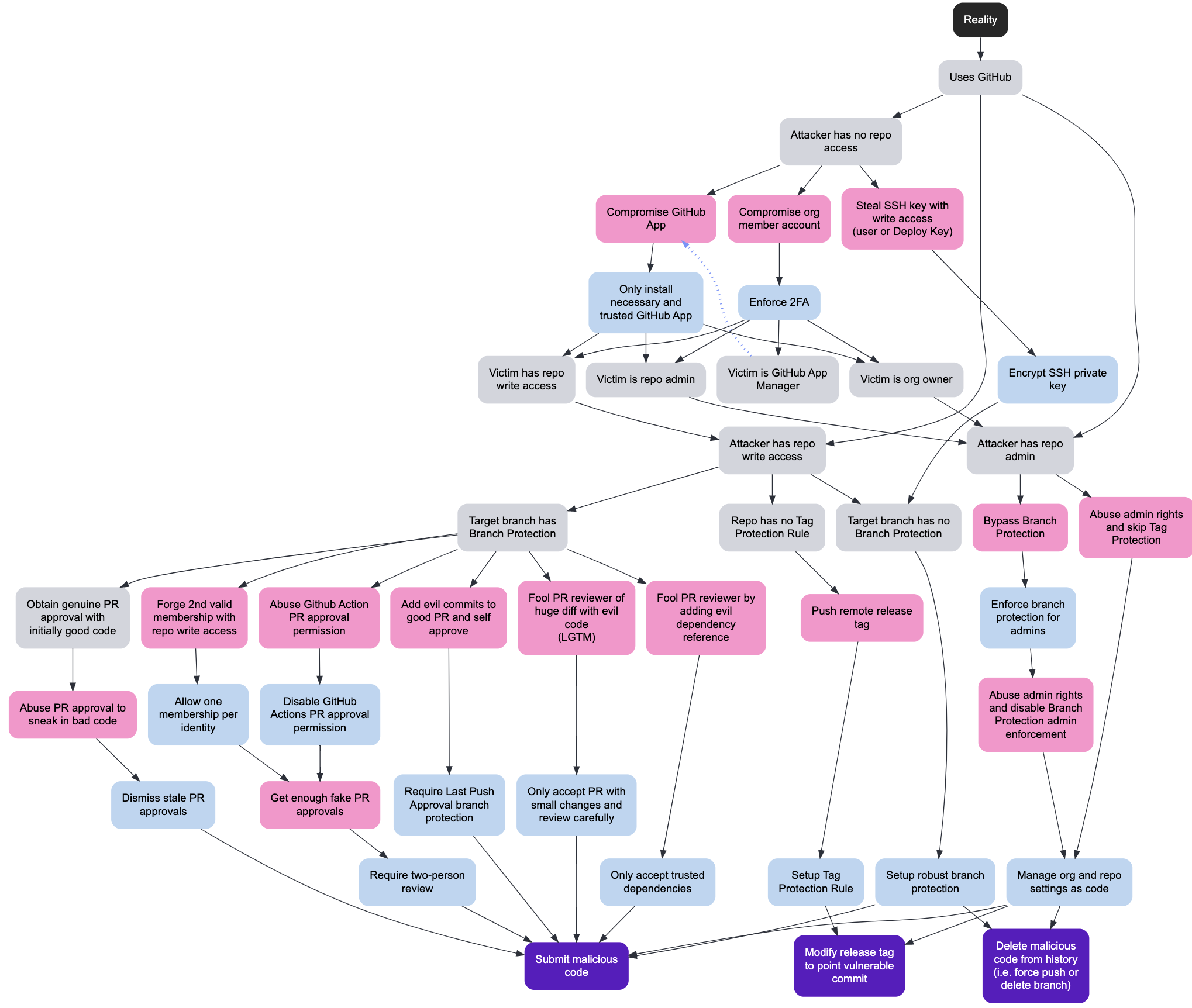
Unveiling Bagel: Why Your Developer's Laptop is the Softest Target in Your Supply Chain
TL;DR We're releasing bagel, an open-source CLI that inventories security-relevant metadata on developer workstations. Credentials, misconfigs, and exposed secrets. It's cross-platform, privacy-first, and designed to help security teams understand the attack surface that modern supply chain adversaries are actively exploiting. Stay tuned for more exciting news about how Boost works to secure every part of the modern software factory (developer endpoints included).